AI Powered Application Security Tools
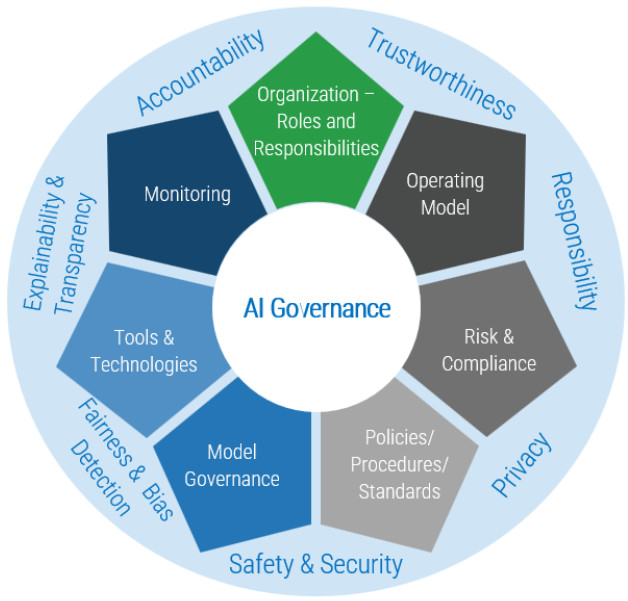
Artificial intelligence has rapidly matured from proof of concept to operational dependency. Today, organizations are leveraging AI models for automating decision-making, optimizing business processes, providing personalized customer engagement, and enhancing internal productivity. However, with the increasing integration of AI models within the business, they also introduce a new risk profile altogether that was not designed to be addressed by traditional application security programs.
AI models are different from traditional software applications. They are probabilistic, data-driven, and dynamically evolving. Their execution lifecycle is no longer determined by code alone but by training data, model structures, deployment contexts, and post-deployment interactions. This has substantially expanded the attack surface for the organization. Threats may emerge from tainted data, unsafe model artifacts, insecure pipelines, or even counterintuitive model behaviors that are incongruent with regulatory or ethical mandates.
AI security testing platforms have emerged as a response to this new paradigm. These platforms are an extension of traditional AppSec programs and introduce new capabilities specifically designed for AI. For the business leader, they provide a mechanism for responsible acceleration of AI adoption, finding a balance between speed and resilience, innovation and risk management.